Date created: Monday, October 27, 2014 10:35:51 AM. Last modified: Monday, June 25, 2018 4:27:33 PM
IOS - AS Options
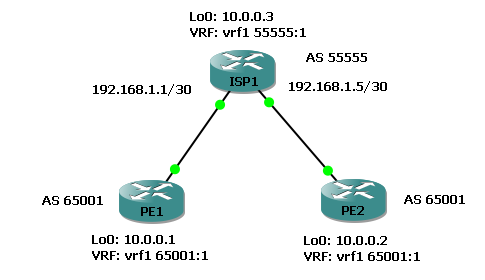
IOS: Testing allowas-in and remove-private-as all replace-as on IOS devices using two CPEs/PEs from an external AS (65001) connected to the local AS (55555).
In both examples below the 10.0.0.2/32 prefix isn't installed to FIB on PE1 because the changes are only being tested on PE2!
allowas-in
All devices run c7200-advipservicesk9-mz.152-4.M7.bin. Configuring "allowas-in" on PE2 on a VPNv4 peering (MPLS Opt B) to upstream router ISP1 allows 10.0.0.1/32 to be received inside vrf1 despite having AS 65001 in the AS path (it's own AS number going against BGP loop prevention).
PE2#show bgp vpnv4 unicast vrf vrf1 | begin Network
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65001:1 (default for vrf vrf1)
*> 10.0.0.1/32 192.168.1.5 0 55555 65001 ?
* 10.0.0.2/32 192.168.1.5 0 55555 65001 ?
*> 0.0.0.0 0 32768 ?
*> 10.0.0.3/32 192.168.1.5 0 0 55555 ?
PE2 (PE1 is the same):
ip vrf vrf1 rd 65001:1 route-target export 65001:1 route-target export 55555:1 route-target import 65001:1 route-target import 55555:1 interface Loopback0 ip vrf forwarding vrf1 ip address 10.0.0.2 255.255.255.255 interface FastEthernet0/1 ip address 192.168.1.6 255.255.255.252 duplex auto speed auto mpls bgp forwarding router bgp 65001 bgp log-neighbor-changes neighbor 192.168.1.5 remote-as 55555 address-family vpnv4 neighbor 192.168.1.5 activate neighbor 192.168.1.5 send-community both neighbor 192.168.1.5 next-hop-self neighbor 192.168.1.5 allowas-in exit-address-family address-family ipv4 vrf vrf1 redistribute connected exit-address-family
ISP1:
ip vrf vrf1 rd 55555:1 route-target export 55555:1 route-target import 55555:1 interface Loopback0 ip vrf forwarding vrf1 ip address 10.0.0.3 255.255.255.255 interface FastEthernet0/0 ip address 192.168.1.1 255.255.255.252 duplex auto speed auto mpls bgp forwarding interface FastEthernet0/1 ip address 192.168.1.5 255.255.255.252 duplex auto speed auto mpls bgp forwarding router bgp 55555 bgp log-neighbor-changes neighbor 192.168.1.2 remote-as 65001 neighbor 192.168.1.6 remote-as 65001 address-family vpnv4 neighbor 192.168.1.2 activate neighbor 192.168.1.2 send-community both neighbor 192.168.1.2 next-hop-self neighbor 192.168.1.6 activate neighbor 192.168.1.6 send-community both neighbor 192.168.1.6 next-hop-self exit-address-family address-family ipv4 vrf vrf1 redistribute connected exit-address-family
In the output above from PE2 the prefix 10.0.0.2/32 is being advertised back to PE2 because it has "allowas-in" configured. To prevent this looping a BGP SoO (Site of Origin) ID can be configured on ISP1. It's an extended community value that is assigned to prefixes learnt from a neighbour. Any prefix with that SoO value will not be sent back to that neighbour:
ISP1:
router bgp 55555
address-family vpnv4
neighbor 192.168.1.6 soo 65001:2
ISP1#show bgp vpnv4 uni vrf vrf1 10.0.0.2
BGP routing table entry for 55555:1:10.0.0.2/32, version 30
Paths: (1 available, best #1, table vrf1)
Not advertised to any peer
Refresh Epoch 1
65001, imported path from 65001:1:10.0.0.2/32
192.168.1.6 from 192.168.1.6 (192.168.1.6)
Origin incomplete, metric 0, localpref 100, valid, external, best
Extended Community: SoO:65001:2 RT:55555:1 RT:65001:1
mpls labels in/out nolabel/16
PE2:
PE2#show bgp vpnv4 uni vrf vrf1 | beg Network
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65001:1 (default for vrf vrf1)
*> 10.0.0.1/32 192.168.1.5 0 55555 65001 ?
*> 10.0.0.2/32 0.0.0.0 0 32768 ?
*> 10.0.0.3/32 192.168.1.5 0 0 55555 ?
remove-private-as [ all [ replace-as ] ]
Since AS 65001 is a private AS range we can use the "remove-private-as" feature on ISP1 by configuring ISP1 with "neighbor 192.168.1.6 remove-private-as all replace-as" under the VPNv4 peer configuration. ISP1 removes any instance of AS 65001 in the AS path for BGP updates AND it replaces them with a value of AS 55555 to keep the AS path length. If the keywords "all replace-as" aren't support on the current IOS image then the private AS is removed but not replaced, unless the AS path contains only private AS numbers in which case no action is performed!
PE2#show bgp vpnv4 unicast vrf vrf1 | begin Network
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65001:1 (default for vrf vrf1)
*> 10.0.0.1/32 192.168.1.5 0 55555 55555 ?
*> 10.0.0.2/32 0.0.0.0 0 32768 ?
*> 10.0.0.3/32 192.168.1.5 0 0 55555 ?
PE2:
router bgp 65001 bgp log-neighbor-changes neighbor 192.168.1.5 remote-as 55555 ! address-family vpnv4 neighbor 192.168.1.5 activate neighbor 192.168.1.5 send-community both neighbor 192.168.1.5 next-hop-self exit-address-family ! address-family ipv4 vrf vrf1 redistribute connected exit-address-family
ISP1:
router bgp 55555 bgp log-neighbor-changes neighbor 192.168.1.2 remote-as 65001 neighbor 192.168.1.6 remote-as 65001 ! address-family vpnv4 neighbor 192.168.1.2 activate neighbor 192.168.1.2 send-community both neighbor 192.168.1.2 next-hop-self neighbor 192.168.1.6 activate neighbor 192.168.1.6 send-community both neighbor 192.168.1.6 next-hop-self neighbor 192.168.1.6 remove-private-as all replace-as exit-address-family ! address-family ipv4 vrf vrf1 redistribute connected exit-address-family
Previous page: IOS - AS-Override
Next page: IOS XR - AS Options