Date created: Tuesday, February 27, 2018 6:00:04 PM. Last modified: Tuesday, February 27, 2018 6:31:03 PM
GREoIPSECoGRE
In the diagram below, CPE1 is connected to PE1. CPE1 connects to PE1 inside the WBMC VRF on PE1 (GRT on CPE1). This is to simulate how an xDSL PPP over L2TP session might be terminated on an LNS (PE1). RADIUS would instruct the LNS (PE1) to terminate the PPP session on Loopback1 inside the WBMC VRF (the underlay VRF in this example).
The requirement here is that CPE1 builds an IPSEC tunnel to a remote firewall inside the customers layer 3 VPN, the VRF called "CH". This is so that the customer can have end-to-end encryption between end site and the central firewall (hub-and-spoke topology).
In the below topology diagram CPE2 will act as the customers central firewall. In the below topology it looks like CPE2 could simply build an IPSEC tunnel to PE1 however, then an end-to-end IPSEC tunnel wouldn't be needed between CPE1 and CPE2. In reality CPE2 (the central firewall device) is connection to a remote PE within the service provider network, and not PE1. CPE2 is connect to PE1 below to save time by not building a service provider core inside GNS3.
The traffic needs to be end-to-end encrypted, CPE2 could not build an IPSEC tunnel to its local PE as the traffic would flow across the service provider core unencrypted.CPE1 must build an IPSEC tunnel to the central firewall, inside the customers layer 3 VPN.
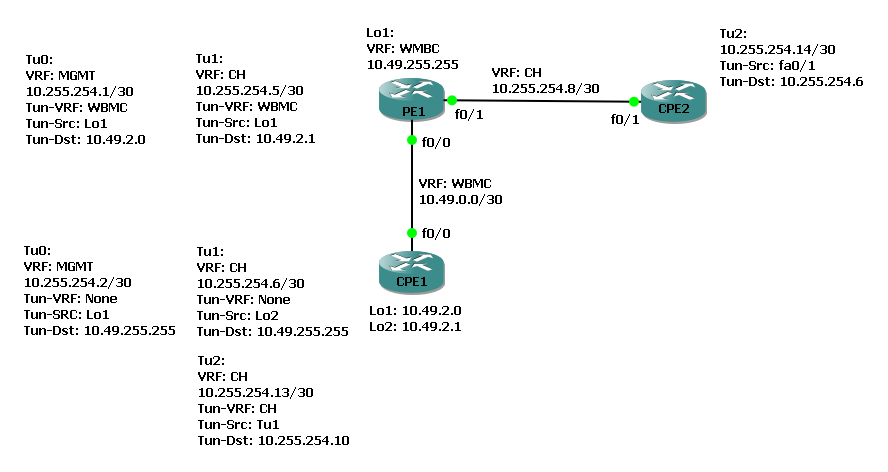
CPE1 builds an underlay GRE tunnel to PE1 inside the GRT on CPE1 and WBMC VRF on PE1. The overlay is inside the customers VRF "CH". This is interface Tunnel1 on CPE1 and PE1.
CPE2 connects to PE1 directly into the CH VRF. CPE2 represents a firewall that is potentially VRF un-aware so all configuration on CPE2 is applied within the Global Routing Table.
CPE1 builds a seconds GRE tunnel with a crypto map applied. The tunnel destination is the IP on CPE2 inside the CH VRF and the source interface is Tu1 inside the CH VRF. This is interface Tunnel2 on CPE1 and CPE2. For Tu2 the underlay and overlay VRF are the same.
Below is the CPE1 config. It also has a GRE tunnel to PE1 which also uses IPSEC, to provide an encrypted management tunnel:
ip vrf CH rd 2:3 route-target export 2:3 route-target import 2:3 ! ip vrf MGMT rd 2:2 route-target export 2:2 route-target import 2:2 ! crypto keyring ADSL-KEY pre-shared-key address 10.49.255.255 key aaaaa ! crypto keyring CUST-KEY vrf CH ! Used for Customer GREoIPSEC tunnel to CPE2 pre-shared-key address 10.255.254.10 key bbbbb ! crypto isakmp policy 10 ! Used for MGMT GREoIPSEC tunnel authentication pre-share ! crypto isakmp policy 20 ! Used for Customer GREoIPSEC tunnel to CPE2 encr aes 256 authentication pre-share group 2 lifetime 28800 ! crypto isakmp profile ADSL-ISAKMP keyring ADSL-KEY match identity address 10.49.255.255 255.255.255.255 ! Lo1 on PE1 inside WBMC VRF ! crypto isakmp profile CUST-PROFILE vrf CH keyring CUST-KEY self-identity address match identity address 10.255.254.10 255.255.255.255 CH ! Fa0/1 on CPE2 inside GRT local-address 10.255.254.6 CH ! ! crypto ipsec transform-set 3DESMD5 esp-3des esp-md5-hmac ! Used for MGMT GREoIPSEC tunnel mode tunnel ! crypto ipsec transform-set AES256SHA esp-aes 256 esp-sha-hmac ! Used for Customer GREoIPSEC tunnel mode tunnel ! crypto ipsec df-bit clear ! no crypto ipsec nat-transparency udp-encapsulation ! crypto ipsec profile ADSL-ROUTERS ! Used for MGMT GREoIPSEC tunnel set transform-set 3DESMD5 ! crypto ipsec profile CUST-IPSEC-PROFILE ! Used for Customer GREoIPSEC tunnel set transform-set AES256SHA set pfs group2 set isakmp-profile CUST-PROFILE ! interface Loopback1 ! Used for MGMT GREoIPSEC tunnel ip address 10.49.2.0 255.255.255.255 ! interface Loopback2 ! Used for Customer GREoIPSEC tunnel ip address 10.49.2.1 255.255.255.255 ! interface Tunnel0 ip vrf forwarding MGMT ip address 10.255.254.2 255.255.255.252 ip mtu 1438 ip tcp adjust-mss 1350 tunnel source Loopback1 tunnel mode ipsec ipv4 tunnel destination 10.49.255.255 tunnel protection ipsec profile ADSL-ROUTERS ! interface Tunnel1 ip vrf forwarding CH ip address 10.255.254.6 255.255.255.252 ip mtu 1438 ip tcp adjust-mss 1350 tunnel source Loopback2 tunnel destination 10.49.255.255 ! interface Tunnel2 ! Tunnel2 run inside of Tunnel1 ip vrf forwarding CH ip address 10.255.254.13 255.255.255.252 ip mtu 1438 ip tcp adjust-mss 1350 tunnel source Tunnel1 tunnel mode ipsec ipv4 tunnel destination 10.255.254.10 tunnel vrf CH tunnel protection ipsec profile CUST-IPSEC-PROFILE ! interface FastEthernet0/0 ip address 10.49.0.2 255.255.255.252 ! ip route 10.49.255.255 255.255.255.255 FastEthernet0/0 ip route vrf CH 0.0.0.0 0.0.0.0 10.255.254.5
Below is the PE1 config. Tu0 to CPE1 is an encrypted GREoIPSEC tunnel. Tu1 to CPE1 is an plain unencrypted GRE tunnel which simply provides CPE1 access to the CH layer 3 VPN on the service provider core. This then allows CPE1 to build an inner (GREoIPSEC) tunnel to CPE2 across the service provider core inside the CH layer 3 VPN:
ip vrf CH rd 1:3 route-target export 1:3 route-target import 1:3 ! ip vrf MGMT rd 1:2 route-target export 1:2 route-target import 1:2 ! ip vrf WBMC rd 1:1 route-target export 1:1 route-target import 1:1 ! crypto keyring ADSL-KEY vrf WBMC ! This is for encrypted management tunnels to CPEs pre-shared-key address 10.0.0.0 255.0.0.0 key aaaaa ! crypto isakmp policy 10 authentication pre-share ! crypto isakmp profile ADSL-ISAKMP vrf WBMC keyring ADSL-KEY match identity address 10.0.0.0 255.0.0.0 WBMC local-address Loopback1 ! crypto ipsec transform-set 3DESMD5 esp-3des esp-md5-hmac mode tunnel ! no crypto ipsec nat-transparency udp-encapsulation ! crypto ipsec profile ADSL-ROUTERS set transform-set 3DESMD5 ! interface Loopback1 ! All CPE-to-LNS tunnels terminate here ip vrf forwarding WBMC ip address 10.49.255.255 255.255.255.255 ! interface Tunnel0 ! To CPE1 ip vrf forwarding MGMT ip address 10.255.254.1 255.255.255.252 ip mtu 1438 ip tcp adjust-mss 1350 tunnel source Loopback1 tunnel mode ipsec ipv4 tunnel destination 10.49.2.0 tunnel vrf WBMC tunnel protection ipsec profile ADSL-ROUTERS shared ! interface Tunnel1 ! To CPE1 ip vrf forwarding CH ip address 10.255.254.5 255.255.255.252 ip mtu 1438 ip tcp adjust-mss 1350 tunnel source Loopback1 tunnel destination 10.49.2.1 tunnel vrf WBMC ! interface FastEthernet0/0 ! This is an Ethernet link to CPE1 but in reality it would be a PPP session inside an L2TP tunnel ip vrf forwarding WBMC ip address 10.49.0.1 255.255.255.252 ! interface FastEthernet0/1 ! Link to CPE2 acting as a central firewall inside the CH layer 3 VPN ip vrf forwarding CH ip address 10.255.254.9 255.255.255.252 ! ip route vrf WBMC 10.49.2.0 255.255.255.255 10.49.0.2 ! These would normally by applied dynamically by RADIUS when CPE1 dials-in ip route vrf WBMC 10.49.2.1 255.255.255.255 10.49.0.2
Finally the CPE2 config is shown below but this is the same as the CPE1-to-PE1 MGMT tunnel config, nothing special to see here:
crypto keyring CUST-KEY ! Used for Customer GREoIPSEC tunnel to CPE1 pre-shared-key address 10.255.254.6 key bbbbb ! crypto isakmp policy 20 encr aes 256 authentication pre-share group 2 lifetime 28800 ! crypto isakmp profile CUST-PROFILE keyring CUST-KEY self-identity address match identity address 10.255.254.6 255.255.255.255 local-address 10.255.254.10 ! crypto ipsec transform-set AES256SHA esp-aes 256 esp-sha-hmac mode tunnel ! crypto ipsec df-bit clear ! no crypto ipsec nat-transparency udp-encapsulation ! crypto ipsec profile CUST-IPSEC-PROFILE set transform-set AES256SHA set pfs group2 set isakmp-profile CUST-PROFILE ! interface Tunnel2 ! Tunnel to CPE1 ip address 10.255.254.14 255.255.255.252 ! /30 to CPE1 Tunnel2 interface ip mtu 1438 ip tcp adjust-mss 1350 tunnel source FastEthernet0/1 tunnel mode ipsec ipv4 tunnel destination 10.255.254.6 ! CPE1 Tunnel1 interface tunnel protection ipsec profile CUST-IPSEC-PROFILE ! interface FastEthernet0/1 ip address 10.255.254.10 255.255.255.252 ip mtu 1438 ip tcp adjust-mss 1350 ! ip route 10.255.254.6 255.255.255.255 10.255.254.9 ! CPE1 Tunnel1 IP via PE1
Previous page: Basic L2TPv3 config with L2 loop
Next page: L2TPv3 Port-Based Xconnect