Date created: Monday, October 27, 2014 5:33:47 PM. Last modified: Monday, June 25, 2018 4:27:27 PM
IOS XR - AS Options
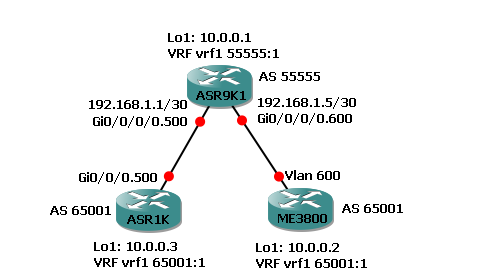
IOS XR Testing as-override, as-path-loopcheck and remove-private-as. Using IOS XRv 5.2.2, IOS 15.3(3)S and IOS-XE 03.12.00.S (IOS 15.4(2)S).
as-path-loopcheck
With traditional IOS in the above topology the ASR9K1 device would advertise 10.0.0.3/32 to the ME3800 device which would then drop it because it's an eBGP route which contains the local AS (65001) in the AS-path (a BGP loop prevention feature). To accept the route on the ME3800 device "allowas-in" would have to be configured.
In IOS XR an outbound feature called "as-path-loopcheck" has been added which would stop the advertisement ever being sent from ASR9K1. In the below example this is enabled under ipv4 unicast address-family within the VRF.
ASR9K1:
vrf vrf1 vpn id 65001:1 address-family ipv4 unicast import route-target 65001:1 export route-target 65001:1 interface Loopback1 vrf vrf1 ipv4 address 10.0.0.1 255.255.255.255 interface GigabitEthernet0/0/0/0.500 description L3-to-ASR1K ipv4 address 192.168.1.1 255.255.255.252 encapsulation dot1q 500 interface GigabitEthernet0/0/0/0.600 description L3-to-ME3800 ipv4 address 192.168.1.5 255.255.255.252 encapsulation dot1q 600 route-policy PASS pass end-policy router static address-family ipv4 unicast 192.168.1.2/32 GigabitEthernet0/0/0/0.500 ! In XR we must have a /32 route to the next-hop, 192.168.1.6/32 GigabitEthernet0/0/0/0.600 ! XR only allocates IGP/NH labels for a /32 address router bgp 55555
bgp router-id 10.0.0.1 address-family ipv4 unicast allocate-label all address-family vpnv4 unicast neighbor 192.168.1.2 remote-as 65001 address-family ipv4 labeled-unicast route-policy PASS in route-policy PASS out send-extended-community-ebgp next-hop-self address-family vpnv4 unicast route-policy PASS in route-policy PASS out next-hop-self neighbor 192.168.1.6 remote-as 65001 address-family ipv4 labeled-unicast route-policy PASS in route-policy PASS out send-extended-community-ebgp next-hop-self address-family vpnv4 unicast route-policy PASS in route-policy PASS out next-hop-self vrf vrf1 rd 65001:1 address-family ipv4 unicast redistribute connected allocate-label all
ASR1K1:
vrf definition vrf1 rd 65001:1 address-family ipv4 route-target export 65001:1 route-target import 65001:1 exit-address-family interface Loopback1 vrf forwarding vrf1 ip address 10.0.0.3 255.255.255.255 interface GigabitEthernet0/0/0.500 encapsulation dot1Q 500 ip address 192.168.1.2 255.255.255.252 mpls bgp forwarding router bgp 65001 bgp router-id 10.0.0.3 bgp log-neighbor-changes neighbor 192.168.1.1 remote-as 55555 address-family ipv4 neighbor 192.168.1.1 activate neighbor 192.168.1.1 next-hop-self neighbor 192.168.1.1 send-label exit-address-family address-family vpnv4 neighbor 192.168.1.1 activate neighbor 192.168.1.1 send-community extended neighbor 192.168.1.1 next-hop-self exit-address-family address-family ipv4 vrf vrf1 redistribute connected exit-address-family
ME3800:
vrf definition vrf1 rd 65001:1 address-family ipv4 route-target export 65001:1 route-target import 65001:1 exit-address-family interface Loopback1 vrf forwarding vrf1 ip address 10.0.0.2 255.255.255.255 exit interface Vlan600 description L3-to-ASR9K1 ip address 192.168.1.6 255.255.255.252 mpls bgp forwarding exit router bgp 65001 bgp router-id 10.0.0.2 bgp log-neighbor-changes neighbor 192.168.1.5 remote-as 55555 address-family ipv4 neighbor 192.168.1.5 activate neighbor 192.168.1.5 next-hop-self neighbor 192.168.1.5 send-label exit-address-family address-family vpnv4 neighbor 192.168.1.5 activate neighbor 192.168.1.5 send-community extended neighbor 192.168.1.5 next-hop-self exit-address-family address-family ipv4 vrf vrf1 redistribute connected exit-address-family
ASR9K1:
RP/0/RSP0/CPU0:ASR9001#show bgp vpnv4 unicast neighbors 192.168.1.6 advertised-routes Network Next Hop From AS Path Route Distinguisher: 65001:1 10.0.0.1/32 192.168.1.5 Local 55555? Processed 1 prefixes, 1 paths
Now "as-path-loopcheck" is enabled on the ASR9K1 and "allowas-in" on the ME3800 and ASR1K1:
conf t router bgp 55555 vrf vrf1 address-family ipv4 unicast as-path-loopcheck out disable
ASR1K1:
conf t router bgp 65001 address-family ipv4 neighbor 192.168.1.1 allowas-in exit-address-family address-family vpnv4 neighbor 192.168.1.1 allowas-in exit-address-family
ME3800:
conf t router bgp 65001 address-family ipv4 neighbor 192.168.1.5 allowas-in exit-address-family address-family vpnv4 neighbor 192.168.1.5 allowas-in exit-address-family
ASR9K1:
RP/0/0/CPU0:ASR9001#show bgp vpnv4 unicast neighbors 192.168.1.6 advertised-routes Network Next Hop From AS Path Route Distinguisher: 65001:1 10.0.0.1/32 192.168.1.5 Local 55555? 10.0.0.2/32 192.168.1.5 192.168.1.6 55555 65001? 10.0.0.3/32 192.168.1.5 192.168.1.2 55555 65001? Processed 3 prefixes, 3 paths
ME3800:
ME3800#show bgp vpnv4 unicast all
BGP table version is 91, local router ID is 10.0.0.2
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65001:1 (default for vrf vrf1)
*> 10.0.0.1/32 192.168.1.5 0 0 55555 ?
* 10.0.0.2/32 192.168.1.5 0 55555 65001 ?
*> 0.0.0.0 0 32768 ?
*> 10.0.0.3/32 192.168.1.5 0 55555 65001 ?
as-override
"as-override" can be usued on the ASR9K1/IOS-XR without the need for "allowas-in" on the IOS/IOS-XE devices.
ASR1K1:
conf t router bgp 65001 address-family ipv4 no neighbor 192.168.1.1 allowas-in exit-address-family address-family vpnv4 no neighbor 192.168.1.1 allowas-in exit-address-family
ME3800:
conf t router bgp 65001 address-family ipv4 no neighbor 192.168.1.5 allowas-in exit-address-family address-family vpnv4 no neighbor 192.168.1.5 allowas-in exit-address-family
ASR9K1:
router bgp 55555 vrf vrf1 address-family ipv4 unicast no as-path-loopcheck out disable exit address-family exit neighbor 192.168.1.2 address-family ipv4 labeled-unicast as-override exit address-family address-family vpnv4 unicast as-override exit address-family exit neighbor 192.168.1.6 address-family ipv4 labeled-unicast as-override exit address-family address-family vpnv4 unicast as-override exit address-family exit
ASR9K1:
RP/0/0/CPU0:ASR9001#show bgp vpnv4 unicast neighbors 192.168.1.6 advertised-ro$ Network Next Hop From AS Path Route Distinguisher: 65001:1 10.0.0.1/32 192.168.1.5 Local 55555? 10.0.0.2/32 192.168.1.5 192.168.1.6 55555 65001? 10.0.0.3/32 192.168.1.5 192.168.1.2 55555 65001? Processed 3 prefixes, 3 paths
ME3800:
ME3800#show bgp vpnv4 unicast all
BGP table version is 115, local router ID is 10.0.0.2
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65001:1 (default for vrf vrf1)
*> 10.0.0.1/32 192.168.1.5 0 0 55555 ?
*> 10.0.0.2/32 0.0.0.0 0 32768 ?
*> 10.0.0.3/32 192.168.1.5 0 55555 55555 ?
remove-private-as
Alternatively the ASR9K1 can be configured to remove the private AS number used in this example (AS 65001) as it is received inbound from the downstream speakers, so they both see updates as having AS 55555 in the PATH. It could be best to break out individual VRFs for the VPNV4 peering rather than blanket removing AS 65001 as that breaks loop prevention.
ASR9K1:
router bgp 55555 neighbor 192.168.1.2 address-family ipv4 labeled-unicast no as-override remove-private-AS inbound exit address-family address-family vpnv4 unicast no as-override remove-private-AS inbound exit address-family exit neighbor 192.168.1.6 address-family ipv4 labeled-unicast no as-override remove-private-AS inbound exit address-family address-family vpnv4 unicast no as-override remove-private-AS inbound exit address-family exit RP/0/0/CPU0:ASR9001#show bgp vpnv4 unicast neighbors 192.168.1.6 advertised-ro$ Network Next Hop From AS Path Route Distinguisher: 65001:1 10.0.0.1/32 192.168.1.5 Local 55555? 10.0.0.2/32 192.168.1.5 192.168.1.6 55555? 10.0.0.3/32 192.168.1.5 192.168.1.2 55555? Processed 3 prefixes, 3 paths
ME3800:
ME3800#show bgp vpnv4 unicast all
BGP table version is 139, local router ID is 10.0.0.2
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 65001:1 (default for vrf vrf1)
*> 10.0.0.1/32 192.168.1.5 0 0 55555 ?
* 10.0.0.2/32 192.168.1.5 0 55555 ?
*> 0.0.0.0 0 32768 ?
*> 10.0.0.3/32 192.168.1.5 0 55555 ? Previous page: IOS - AS Options
Next page: ASN Filtering