Date created: Thursday, September 24, 2015 10:30:17 AM. Last modified: Wednesday, September 27, 2017 3:44:06 PM
VASI Inter-VPN Routing
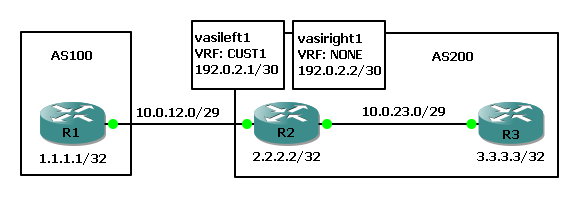
Customer 1 carries their Internet routing in within a VPN (CUST1 VRF in this example). At some point they need to break out of the VPN to reach the public Internet. VRF-Aware-Service-Interfaces can route between VRFs or between a VRF and the Global Routing Table (in the example below).
In the following example the customer has a link from R1 (CPE) to R2 (PE) inside their Inet VPN "CUST1" to exchange routing information with other customer CPEs but VASI interfaces are used to also break out into the public Internet (the GRT for the provider on R2 and R3).
R1
int fa0/0 ip addr 10.0.12.1 255.255.255.248 exit int lo0 ip addr 1.1.1.1 255.255.255.255 exit router bgp 100 bgp router-id 1.1.1.1 bgp log-neighbor-changes neigh 10.0.12.2 remote-as 200 address-family ipv4 uni nei 10.0.12.2 activate nei 10.0.12.2 next-hop-self redist conn exit exit
R2
ip vrf CUST1 description Custome 1 Inet VPN rd 2.2.2.2:100 route-target both 100:100 exit int fa0/0 descrip Link to R1 ip vrf forwarding CUST1 ip addr 10.0.12.2 255.255.255.248 exit int fa0/1 descrip Link to R3 ip addr 10.0.23.2 255.255.255.248 ip ospf 1 area 0 exit int lo0 ip addr 2.2.2.2 255.255.255.255 exit router ospf 1 router-id 2.2.2.2 passive-interface default no passive-interface fa0/1 network 2.2.2.2 0.0.0.0 area 0 exit router bgp 200 bgp router-id 2.2.2.2 bgp log-neighbor-changes nei 3.3.3.3 remote-as 200 address-family ipv4 uni nei 3.3.3.3 activate nei 3.3.3.3 next-hop-self exit address-family ipv4 vrf CUST1 nei 10.0.12.1 remote-as 100 nei 10.0.12.1 activate nei 10.0.12.1 next-hop-self nei 10.0.12.1 default-information originate exit exit
R3
int fa0/1 descrip Link to R2 ip addr 10.0.23.3 255.255.255.248 ip ospf 1 area 0 exit int lo0 ip addr 3.3.3.3 255.255.255.255 exit router ospf 1 router-id 3.3.3.3 passive-interface default no passive-interface fa0/1 network 3.3.3.3 0.0.0.0 area 0 exit router bgp 200 bgp router-id 3.3.3.3 bgp log-neighbor-changes nei 2.2.2.2 remote-as 200 address-family ipv4 uni nei 2.2.2.2 activate nei 2.2.2.2 next-hop-self exit exit
At this point R1 and R2 are peered inside the CUST1 VRF and R2 and R3 are peering inside the GRT. R2 is sending R1 a default route inside the CUST1 VRF and R1 is sending R2 it's loopback 1.1.1.1/32. R2 needs to advertise 1.1.1.1 into the GRT so that R3 has visibility of it, then R1 and R3 loopbacks can ping (which we can assume are public IPs and this is proving Internet reachability from inside the customer Inet VPN).
On R2
interface vasileft1 ip vrf forwarding CUST1 ip address 192.0.2.1 255.255.255.252 no keepalive exit interface vasiright1 ip address 192.0.2.2 255.255.255.252 no keepalive exit router bgp 200 nei 192.0.2.1 remote-as 200 nei 192.0.2.1 route-reflector-client nei 192.0.2.1 next-hop-self nei 192.0.2.1 default-originate nei description VASI-Inside-VRF-CUST1 address-family ipv4 vrf CUST1 bgp router-id 192.0.2.1 nei 192.0.2.2 remote-as 200 nei 192.0.2.2 activate nei 192.0.2.2 next-hop-self nei 192.0.2.2 route-reflector-client nei 192.0.2.2 description VASI-Inside-GRT exit-address-family exit
Previous page: Route Distinguisher Significance
Next page: VRF & L3VPN Packet Leaking